
The more security and backup you have in place for your computer system, the more protected you are against cyber-crime.
By: Jennifer Schuler
Technical Writer
Let’s face it – there is no such thing as too much protection or backup for your computer, your business documents, and your email. Recently, there has been a lot of buzz about a type of “ransom-ware” called CryptoLocker Trojan. Yet according to Gregg Keizer in his November 19, 2013 article for Computerworld, “The CryptoLocker Trojan is an evolution of ‘ransom-ware,’ not a revolutionary change from past criminal attempts to extort money from PC owners …”
Keizer states that all the media attention given CryptoLocker Trojan is a bit exaggerated and quotes John Shier, a senior security advisor for U.K.-based Sophos. In a November 19, 2013 interview Shier gave, he says, “There is a bit of hype, actually it’s [CryptoLocker] only the latest incarnation of ransom-ware.”
Ransom-ware is a type of malware which not only encrypts files on the system’s hard drive, or restricts access to an infected computer system – it also demands that a “ransom” be paid to the creator of the malware for the restriction to be removed, and files decrypted, so they can once again be opened. Referred to as “scare-ware,” sometimes the messages displayed on a user’s computer screen can be quite threatening and are intended to be so – intimidating or scaring the user into paying. Only the malware writer knows the needed private decryption key.
Crime-ware has been traced back as far as 1989, yet has been in active circulation since about 2005. It was initially popular in Russia, though the use of ransom-ware scams has spread worldwide. According to Wikipedia, software vendor McAfee released data showing it had collected over 250,000 samples of ransom-ware in the first quarter of 2013 – more than double the number obtained from the first quarter of 2012!
Details of how ransom-ware typically works to infect a computer system can be disturbing to read. Ransom-ware often enters a computer system when a user clicks on a questionable website or email/attachment, downloads an infected file, or has an unprotected network. It then multiplies as a trojan or conventional computer worm and runs a payload such as one that will begin to encrypt personal files on the hard drive. The ransom-ware payloads then display notices that appear to have come from legitimate companies or law enforcement agencies, including the FBI. The notices falsely claim that the system has been used for illegal activities or contains illegal content – for example pornography, and pirated software or media. Some ransom-ware payloads even imitate Windows XP’s product activation notices, falsely stating that the user’s computer Windows installation is counterfeit or needs to be reactivated to work effectively. In some cases, the virus uses your webcam to take a picture of you and display it back – even more frightening!
Interestingly, although CryptoLocker, which first appeared earlier this year, is not a revolutionary new ransom-ware, it has generated more notable reports than any of its predecessors. What it has done is built upon similar previous ransom-ware programs and then use new tactics and techniques to extort money from users. To do so, CryptoLocker uses public-key cryptography. Once it has infected a computer system, it attempts to connect to a command-and-control server – generating a pair of public and private digital keys, and uploading the key to the server. Though not the first ransom-ware program to rely on a pair of digital keys (one public and stored on the compromised PC, and one private which is not), CryptoLocker goes a step further and ships that private key to the cyber-criminals who hold it until payment is received from the user.
The cyber-criminals tell you your computer will be permanently locked, or you may even be arrested, if you don’t pay a $200 fine. The ransom-ware will demand payment and threaten to delete the private key if payment is not received within 3 days. Sometimes ransom prices can reach into four figures. Users must pay to obtain the private key and begin decrypting files, which computer analysts have said is very difficult to repair due to the extremely large key size CryptoLocker uses. It may even be impossible to remove if it locks up your PC.
A frightening example of this form of scare ware was presented in an article by John Matarese, published on the website SearchSecurity as part of the “Don’t Waste Your Money” series. As a woman sat down at her PC early this year, an unknown web page with the FBI logo appeared on her screen – along with an alert stating that she had visited an illegal website. Therefore, she was being locked out of her web access until she paid a $200 fine through a Green Dot Money Pack card.
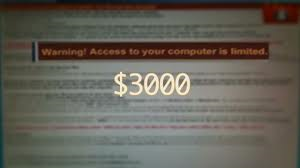
Ransom-ware often forces victims to pay in order to obtain access to their computer and its files again.
What aroused her suspicion is the mode by which the “FBI” wanted payment delivered – through a reloadable debit card from a drugstore. It was then that she knew this was online extortion at its worst. Fortunately, the woman and her husband were able to Google search on their smartphones for a way to remove what is being called the “FBI Green Dot Moneypack Virus.”
This couple was fortunate they were able to conduct a self-clean, system restore on their own. Yet this is not always the case in such ransom-ware situations. If this happens to you, do not touch your computer or manipulate it in any way until you have searched on another computer for the fix. Better yet, call a computer repair shop for assistance from a trained expert. It is reported by security experts that removing CryptoLocker now requires a full wipe of your hard drive and, therefore, losing all your files.
Stories such as this one remind us that it is very important to be absolutely sure of the email, attachment, downloadable file, or website source with which you are about to interact. It takes just one wrong click to wipe out scores of valuable personal and business data from your computer system. CryptoLocker can even search for files to encrypt on USB sticks and shared network drives. CryptoLocker’s encryption capabilities are much more sophisticated than previous versions of ransom-ware and therefore more difficult, if not impossible, to repair and restore.
Any email or online notice from the government is a scam, especially if it does not include your name in the notice. That is not how government agencies such as the FBI or IRS operate. They will not email you or post notices on your computer screen accusing you of wrongdoing, violating laws, or committing a crime. Rather, they will write – or even show up at your door!
Some words of caution:
- Never wire money or pay by Pay Pal, Green Dot card, or any other payment method to a threat. The more ransom that is paid to these cyber-criminals and extortionists, the more the trend continues. CryptoLocker, and other ransom-ware viruses, won’t go away until there is no profit to be made!
- Never open strange, unexpected attachments to any email you receive.
- Put protective measures in place on your computer system to avoid any form of ransom-ware or malware in the first place.
- Conduct regular computer system backups.
- Use a reputable technology company to protect your computers through security-based programming.
- Add another layer of authentication to sensitive files, or encrypt and password-protect them.
Ransom-ware such as CryptoLocker has very sophisticated encryption algorithms and thousands of domains coming online every day that serve the encryption keys – frequently changing binaries, and even has the ability to infect machines via another attack campaign. Using the above protective security measures, however, can prevent CryptoLocker from accessing and taking over your computer system.
Businesses usually have protective security measures and defenses in place, including robust spam filters, attachment blocking and multiple layers of security. These type of ransom-ware viruses are actually a greater threat to the everyday PC user – to consumers, since often they don't have those kinds of protection tools.
Unfortunately, users facing CryptoLocker likely have few options for successful restoration of their files. While the malware itself can be relatively easily scrubbed from the system, the already-encrypted files will remain encrypted since it is nearly impossible to crack the encryption.
If your computer system does become infected:
- Unplug your computer immediately. On a desktop PC, quick action may limit the damage because it takes time for the malware to encrypt every file it has targeted.
- Do not use the infected computer to search for ways to repair the damage.
- Contact Provident Technology for restoration assistance.
Due to the reported success of the CryptoLocker, there is the possibility that this type of ransom-ware virus increases. Don’t leave your business’ computer system or personal PC unprotected!
Provident Technology offers solid protection and security through our Managed Services. Enterprise level Spam and Anti-Virus Filtering of Email provides anti-virus protection tools that filter spam and malicious programs out of email before they are passed to the end user’s mailbox. We also offer Fully Compliant Email Archiving – providing the preservation, protection, and restoration features you need to safeguard intellectual property.
Additionally, Provident Technology’s Managed Backup gives you peace of mind knowing that our managed backup services cover more than just copying your data. With Provident OneManage, your entire data center can be replicated to failover equipment that takes over seamlessly in the event of hardware failure on your primary equipment. Through continuous data mirroring, Provident OneManage continuously captures data on desktops and servers, providing near real time protection as data is written to Provident Technology’s NOC. Data captures are VSS aware, occurring at the block level. Data Recovery, Failover Virtualization, Bare Metal Recovery, Granular Exchange Recovery, Offsite Transfer/Data Replication, and Monitoring and Management are also available.

Provident Technology will secure your computer system and protect your valuable business and personal files!
Click here to visit Provident Technology’s Managed Backup page and learn more about protecting your business. Prevent your business’ computer system from falling victim to any form of ransom-ware – contact us today!



You must be logged in to post a comment.